The United States and international partners are blaming China with “high confidence” for the cyber campaign exploiting zero-day vulnerabilities in Microsoft Exchange reported by the company in March and announced new joint measures to “strengthen our collective cyber resilience and security cooperation,” a senior administration official told reporters late Sunday.
“We’ve raised our concerns about both the Microsoft incident and the PRC’s broader malicious cyber activity with senior PRC government officials, making clear that the PRC’s actions threaten security, confidence, and stability in cyberspace,” the official said. “The U.S. and our allies and partners are not ruling out further actions to hold the PRC accountable.”
The official said that the investigation behind the attribution “really gave us new insights on the MSS’s work and on the kind of aggressive behavior that we’re seeing coming out of China.” The “breadth of compromises, tens of thousands of systems around the world” also delayed attribution for the Microsoft Exchange hack until now.
“Individuals on the MSS payroll” made “a large ransom request made to an American company,” the official said without revealing further details.
The official said the administration’s response intends to “show how the PRC’s MSS — Ministry of State Security — uses criminal contract hackers to conduct unsanctioned cyber operations globally, including for their own personal profit.”
“Their operations include criminal activities, such as cyber-enabled extortion, crypto-jacking, and theft from victims around the world for financial gain,” the official added. “In some cases, we’re aware of reports that PRC government-affiliated cyber operators have conducted ransomware operations against private companies that have included ransom demands of millions of dollars.”
While there are some visible connections between Russian intelligence services and individual cyber criminals, the official said that China’s MSS “use of criminal contract hackers to conduct unsanctioned cyber operations globally is distinct.”
Today’s response to the Microsoft Exchange hack included NATO condemning China’s cyber activities for the first time as part of a collaborative response with the United States, the European Union, the United Kingdom, Australia, Canada, New Zealand, and Japan.
“We think we’re at that first important stage of bringing awareness and buy-in to this attribution, and focusing us together on our collective security efforts, promoting network defense, and other actions needed to disrupt these threats,” the senior administration official said.
The agreement “highlights just the number of victims of Chinese malicious cyber activity and the degree to which countries increasingly recognize that there’s power in collective defense and that working together will be just far more effective in countering this activity.”
Secretary of State Tony Blinken said in a statement today that the United States is “working with our partners and allies to promote responsible state behavior in cyberspace, counter cybercrime, and oppose digital authoritarianism,” and will be “providing support to countries that are committed to building their capacity to protect their digital networks, investigate and impose consequences on malicious cyber actors, and participate in international conversations on cyber policy.”
“These efforts will enhance global security and stability in cyberspace,” Blinken said. “The State Department is committed to driving this agenda forward, and we call upon all states that wish to see greater stability in cyberspace to join us in these efforts.”
The National Security Agency, DHS Cybersecurity and Infrastructure Security Agency, and FBI jointly issued an advisory today detailing mitigations — including patching, enhanced authentication and monitoring, and using protection — for more than 50 tactics, techniques, and procedures used by China to target U.S. and allied networks.
“One significant tactic detailed in the advisory includes the exploitation of public vulnerabilities within days of their public disclosure, often in major applications, such as Pulse Secure, Apache, F5 Big-IP, and Microsoft products,” the NSA said.
The threat overview document says the intelligence community has assessed that China “leverages cyber operations to assert its political and economic development objectives,” and “Chinese state-sponsored cyber actors aggressively target U.S. and Allied political, economic, military, educational, and critical infrastructure (CI) personnel and organizations to steal sensitive data, emerging and key technology, intellectual property, and personally identifiable information (PII).”
While operations have included “compromising telecommunications firms, providers of managed services and broadly used software, and other targets potentially rich in follow-on opportunities for intelligence collection, attack, or influence operations,” agencies also “have observed increasingly sophisticated Chinese state-sponsored cyber activity targeting political, economic, military, educational, and CI personnel and organizations.”
“Target sectors include managed service providers, semiconductor companies, the Defense Industrial Base (DIB), universities, and medical institutions,” the advisory notes.
Leaders of businesses and organizations should “drive a culture of cybersecurity investment and strategy,” ensure they have well-honed response plans, and stay informed about current developments in Chinese malicious cyber activity to “ensure security personnel monitor key internal security capabilities and can identify anomalous behavior.”
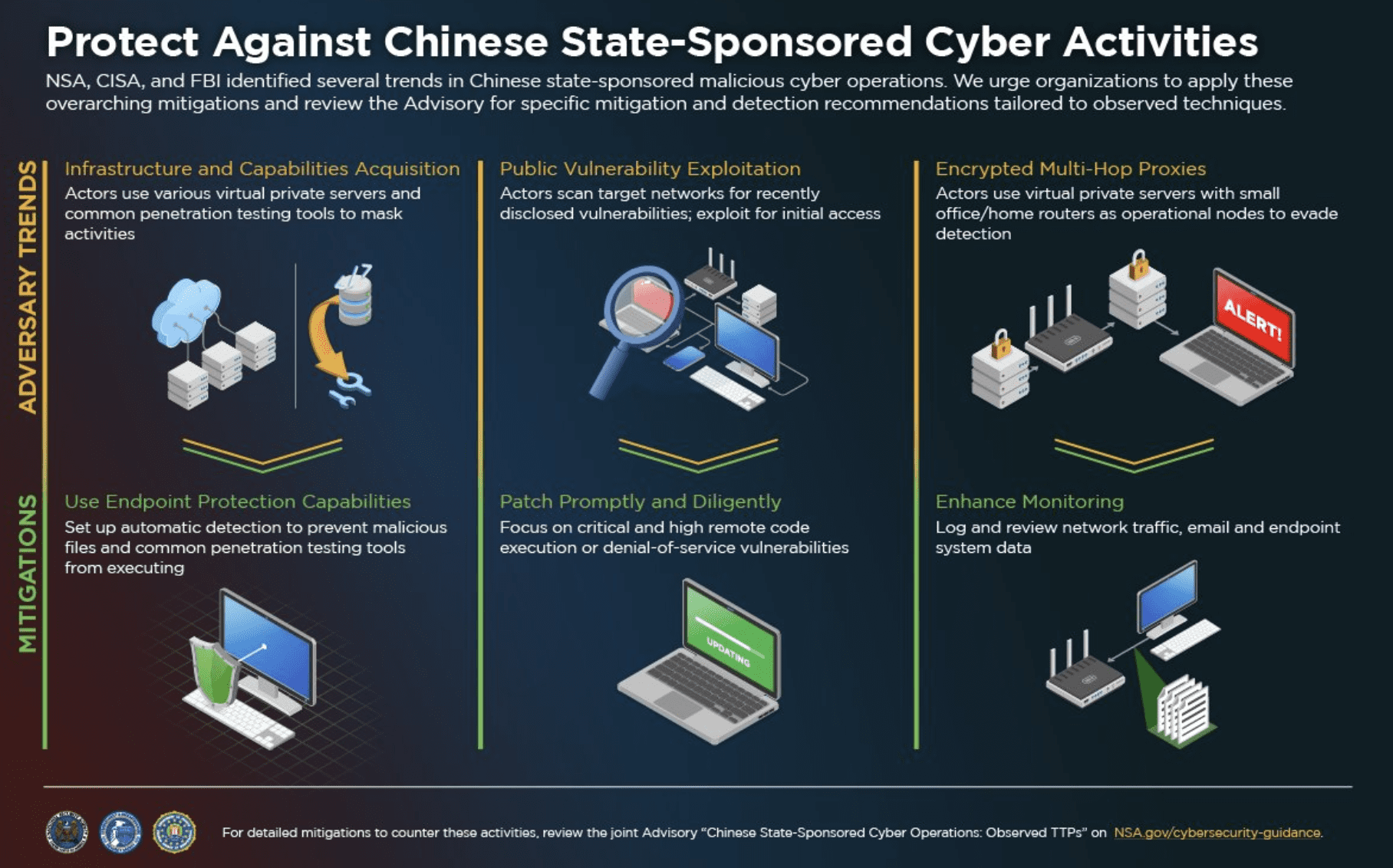
A longer document details observed Chinese cyber ops — including conducting reconnaissance on Microsoft 365, using VPSs from cloud service providers to host malware, using Cobalt Strike and tools from GitHub on victim networks, exploiting known vulnerabilities in Internet-facing systems, conducting spearphishing campaigns, gaining credential access into victim networks by using legitimate but compromised credentials, and more — along with corresponding recommendations for detection and mitigation.
NSA said the information was intended to build upon their October advisory detailing 25 vulnerabilities being exploited by Chinese state-sponsored malicious cyber actors.
CISA and the FBI released Joint Cybersecurity Advisory: TTPs of Indicted APT40 Actors Associated with China’s MSS Hainan State Security Department to help network defenders identify and remediate intrusions.
The Justice Department today said four Chinese nationals have been indicted in “a campaign to hack into the computer systems of dozens of victim companies, universities and government entities in the United States and abroad between 2011 and 2018,” focusing on “information that was of significant economic benefit to China’s companies and commercial sectors, including information that would allow the circumvention of lengthy and resource-intensive research and development processes.”
“The defendants and their Hainan State Security Department (HSSD) conspirators sought to obfuscate the Chinese government’s role in such theft by establishing a front company, Hainan Xiandun Technology Development Co., Ltd.,” DOJ said.
Ding Xiaoyang, Cheng Qingmin, and Zhu Yunmin are charged with coordinating and managing a team of hackers at Hainan Xiandun and other MSS front companies. Wu Shurong, a hacker at Hainan Xiandun, is charged with supervising other hackers while creating malware and hacking hacked into computer systems operated by foreign governments, companies and universities.
“The conspiracy’s hacking campaign targeted victims in the United States, Austria, Cambodia, Canada, Germany, Indonesia, Malaysia, Norway, Saudi Arabia, South Africa, Switzerland and the United Kingdom. Targeted industries included, among others, aviation, defense, education, government, health care, biopharmaceutical and maritime,” DOJ said. “Stolen trade secrets and confidential business information included, among other things, sensitive technologies used for submersibles and autonomous vehicles, specialty chemical formulas, commercial aircraft servicing, proprietary genetic-sequencing technology and data, and foreign information to support China’s efforts to secure contracts for state-owned enterprises within the targeted country (e.g., large-scale high-speed railway development projects). At research institutes and universities, the conspiracy targeted infectious-disease research related to Ebola, MERS, HIV/AIDS, Marburg and tularemia.”






