The National Security Agency (NSA) has released the Cybersecurity Information Sheet (CSI) “Procurement and Acceptance Testing Guide for Servers, Laptops, and Desktop Computers” encouraging U.S. Government departments and agencies operating National Security Systems (NSS) to implement a robust supply chain risk management strategy.
Enterprise computing systems should be procured with a robust set of security capabilities that are tested before acceptance. The CSI details implementation of a supply chain risk mitigation process that utilizes Trusted Platform Modules (TPMs) and Platform Certificates.
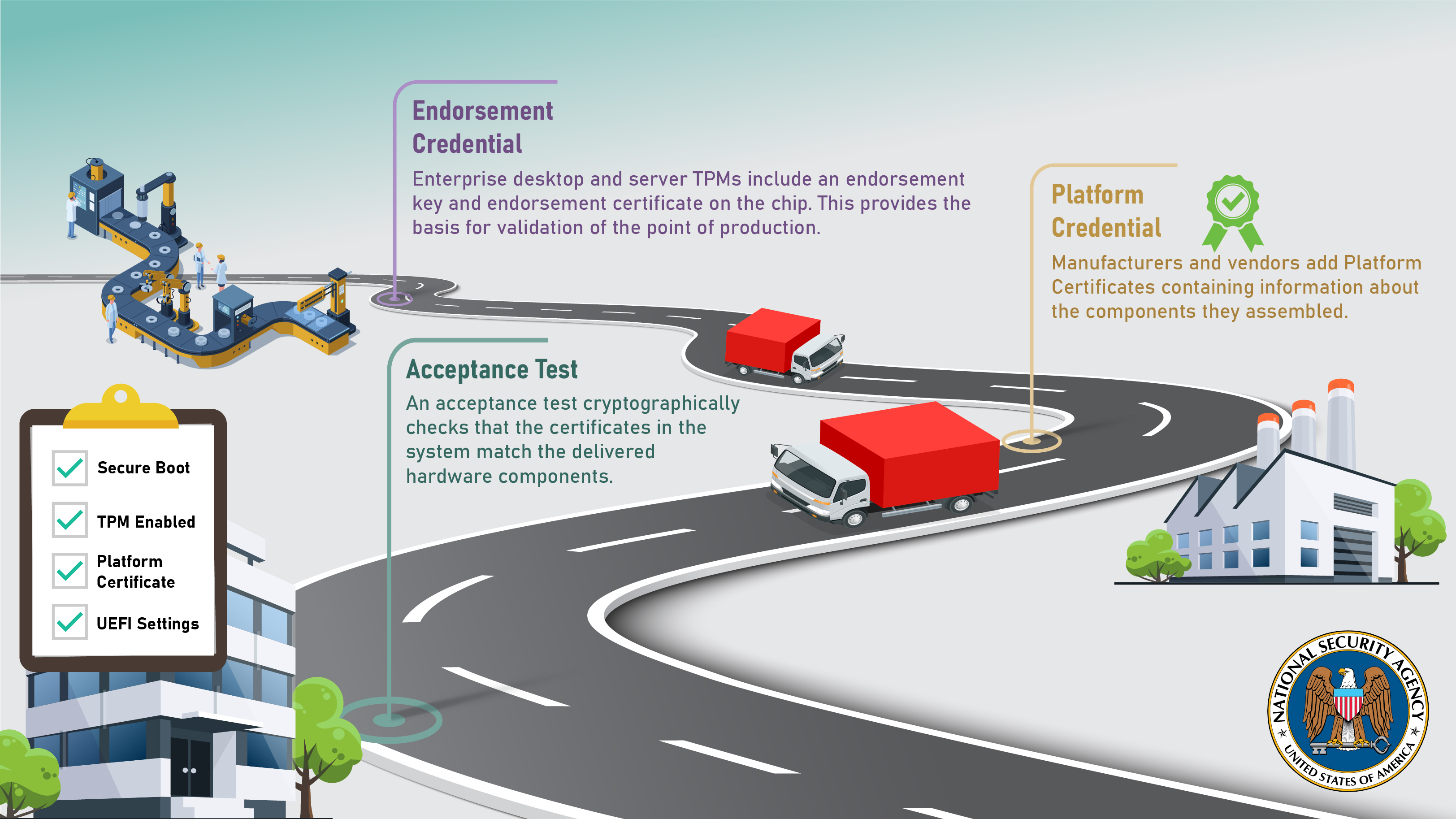
A TPM is a small security chip embedded in most enterprise computing systems. The TPM stores keys associated with certificates created by vendors and manufacturers. The keys are then used during acceptance testing to validate the integrity of the computing system.
The Department of Defense Instruction (DoDI) 8500.01, “Cybersecurity,” requires the Department of Defense (DoD) to include a TPM with computer asset purchases. As part of the NSS procurement process, this requirement should be included when devices are ordered, according to the CSI.
Using TPMs as recommended in the CSI will extend validation capabilities to hardware components provided by vendors and manufacturers. The CSI informs procurement professionals and original equipment manufacturers (OEMs) about provisions and capabilities to support the testing and validation of enterprise computing systems.
As indicated in the CSI, the Platform Certificates are a vital part of the supply chain acceptance test. Platform Certificates allow vendors and manufacturers to add their own certificates during different phases of the devices’ manufacturing process. It acts as a digital certificate that binds a device or component(s) to a specific manufacturer, model, and serial number.
The CSI indicates acceptance testing should be implemented to validate the integrity of devices and ensure they are meeting procurement and security requirements. The automated acceptance test cryptographically checks and assesses the certificates delivered in the device. It further checks if the TPM is enabled and activated, and also validates the Platform Certificates from manufacturers and vendors.
NSA encourages the inclusion of Platform Certificates and an automated acceptance test in the procurement contract of enterprise computing systems. These contracts should include a clause requiring that devices pass the acceptance test. A device that fails should be considered defective and returned to the factory.
Visit our full library for more cybersecurity information and technical guidance.




